Classic Europeans on the Internet trying to make fun of [bad thing that happens in the US] without realising it also happens in Europe
If you work between 6 to 9 hours a day, you are entitled to a 30-minute break after no later than 6 hours. If you work more than 9 hours a day, the break is extended to 45 minutes. Labour law prohibits taking the break at the end of the day’s work in order to leave earlier.
As soon as your daily working time reaches 6 hours immediately, you must have a break of at least 20 minutes consecutive
The break is granted:
- Either immediately after 6 hours of work[, or]
- before this 6-hour period is completed
Employers can say when employees take rest breaks during work time as long as:
- the break is taken in one go somewhere in the middle of the day (not at the beginning or end)
- workers are allowed to spend it away from their desk or workstation (ie away from where they actually work)
American states set their own labour laws, but the ones of the state where I live (Oregon) are actually far more generous than comparable ones in Europe. I am entitled by law during an eight-hour working day to one 30-minute lunch break (not paid) and two additional 10-minute breaks (counts as time worked and is paid). Meaning I get 50 minutes of breaks in a day and the employer has to pay me during 20 minutes of those breaks. My employment contract actually gives me a 1-hour lunch break in addition to the two 10-minute breaks, which isn’t required by law but is not uncommon.







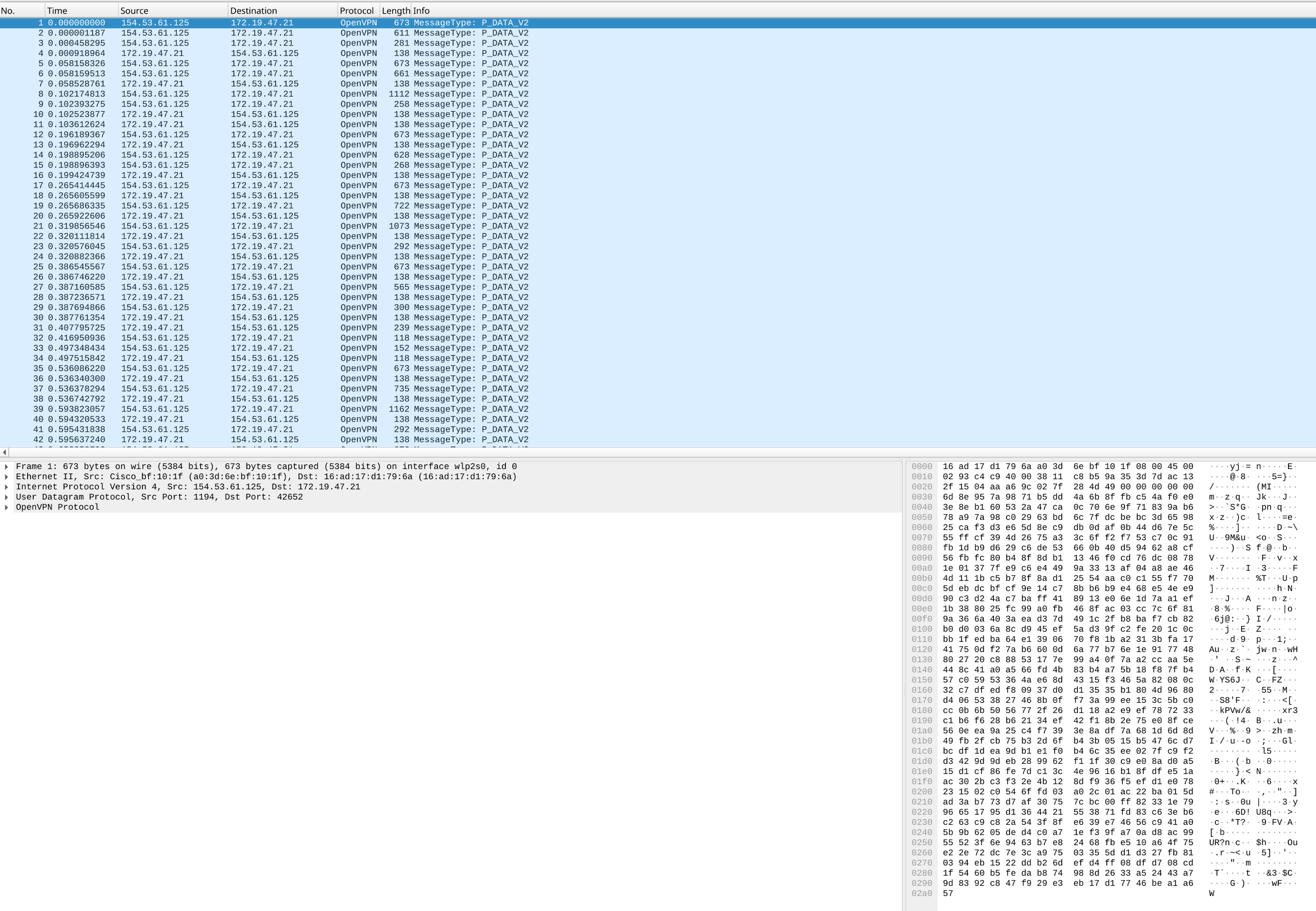




Please read the article. I hate when people upvote bullshit just because it says things they like to hear. I dislike Elon Musk as much as anyone else, but the jury’s findings were this: